One day last week we got the call. A client infected with a virus. Now, we’ve seen our fair share of viruses before, so at worst we were thinking that this virus is going to require us reinstalling a workstation’s operating system. And other than being an annoyance, all would be well after some TLC. This couldn’t have been farther from the truth.
The virus comes in via email but you can also get it, by going to an infected website. Our client believes they got it, by double clicking on an attachment that came in via email. Now here is the kicker. It got past 4 different Anti-virus programs that their email gets filtered by at a 3rd party anti-spam service provider, and past their own AV. It then proceeded to do the following:
- It installed itself into the user’s %APPDATA% personal profile area. This is a temporary work area where a lot of programs, including Google’s Chrome and Adobe’s Flash player install themselves to run from. In fact there are a LOT of programs that put stuff into this folder. Simply go START, RUN and type %APPDATA% to see for yourself.
-
It contacted a Command and Control server up in the cloud, to get a 2048bit encryption key for its next task:
Bleeping Computer’s CryptoVirus FAQ
The virus proceeded to encrypt all the user data it could get its little digital paws on. Small side note. How strong is 2048 bit encryption? Never mind that, what the heck IS encryption? The simplest analogy is imagine having a lock on your data. That lock has X number of possible keys, associated with that lock. In the case of banks and using the Internet to do your daily banking, they are happy to use SSL encryption that uses 2128 number of keys. Oh oh, math. I’m going to be REALLY gentle here.
What the heck is 2128?
Its 2 to the power of 128.
22 is 2 x 2 or 4.
25 is 2x2x2x2x2 or 32.
So 2128 is 2 multiplied by itself 128 times.That number (2128) turns out to be 340,282,366,920,938,463,463,374,607,431,768,211,456 number of different keys that you would have to try in order to BREAK 128 bit SSL encryption.
Now for you or I, brute forcing or manually trying every key, even with all the computers we could get our hands on might be tough. Not so, for the NSA or other spy agencies.
But 22048 bit encryption?
That is 2 mulitplied by itself 2048 times.
That winds up to be a CRAZY 3.2 x 10616or 32 followed by 615 zeroes.That is an INSANE amount of possible keys for that lock. The power of 2 is certainly an amazing thing.
So IF your data gets encrypted by this virus, forget about trying to DECRYPT it yourself or downloading a tool to do it. It ain’t gonna happen.
Let’s continue
- After it has encrypted all of your local data (pictures – jpgs, gifs, tiffs, documents – xls, doc, pdf, etc.) it goes searching for MORE of the same on any NETWORK drives that your computer might be attached to. No big deal if you happen to work on your own. But if your computer gets infected at work? OMG. Yeah.
-
Once it has finished pillaging your digital treasures, the virus displays the picture shown above. It wants some money.
Ransom Time You want your data back? Guess what? They’ll give you the key to unlock your encrypted data for some cash. So this should be easy. Just follow the money trail, you say. Except there isn’t one. The “thieves” want nothing less than BitCoin or MoneyPaks for the return of your data. And as in true Ransom fashion, you only have less than 100 hours to provide them with those funds. Otherwise they wipe the key to your data. Both BitCoin and MoneyPak are anonymous Internet currencies that have sprung up in the last decade and are SO prevalent that the world’s first BitCoin ATM sprung up in Vancouver recently.
-
So now you’re stuck. Pay up, and risk losing money AND your data. Or go to your backups and get the last known version of those now encrypted but useless files.
If you decide to pay because you have NO BACKUPS, the Internet reports that recovery rates have been positive, though not 100%. You may get the bulk of your family wedding pictures or even your PowerPoint presentations, or you may not. But be sure to make a LOT of copies of them once you get the files back.
If you have recent backups then simply get a reputable firm to scrub your machine for you. If all of the data was encrypted, then it simply needs to be DOD wiped, the Operating system reinstalled and away you go.
One last hope if you haven’t a good recent backup. If you run any version of Windows 7, you actually may have a backup present, but you didn’t even know about it. It’s called SYSTEM PROTECTION. By default it is turned on, but the frequency with which it runs and the number of times it runs depends upon how often you change your system. So how do you access those OTHER files? Simply find the file that was encrypted (in My Documents folder or wherever you save your files locally) and right click on it and go to properties. You should see this:
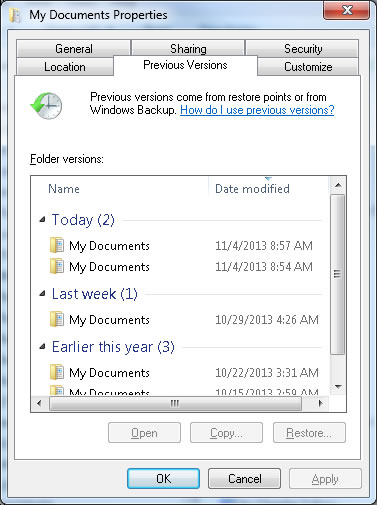
Highlight the file you want, then click on restore. In my case it was going to overwrite whatever file I currently had in place so MAKE SURE that you have made copies of your current files to some other location. Even if they are encrypted. Just don’t cut and paste them elsewhere, as you would then lose the ability to restore an old copy of that file since it moved elsewhere.
If you don’t see any previous versions, but you ARE running Windows 7, you may need Shadow Explorer, a shareware utility that views previous versions of files that you can’t see using the above method. Another amazing tool.
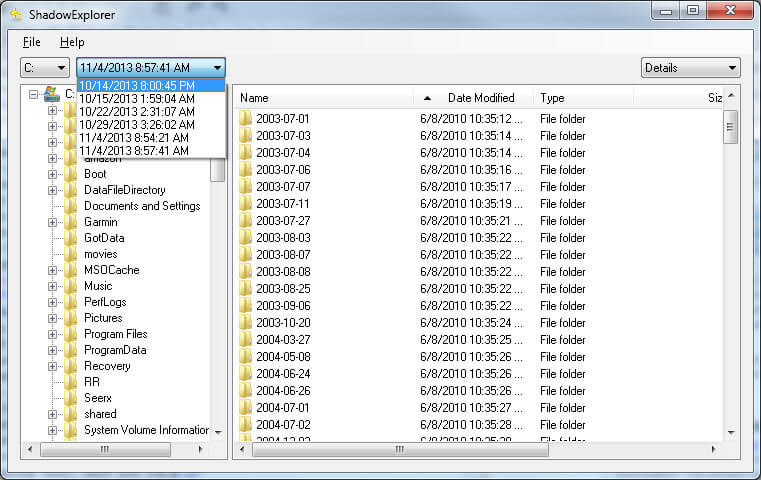
Once you open up Shadow Explorer, browse to where your files USED to be. Then in the top LEFT HAND CORNER of Shadow Explorer, choose the date you want to go back to. If you’re lucky, you’ve got an unecrypted copy of your data, pictures, etc in there.
How can I prevent this from affecting my computer / network? A great resource has been the Bleeping Computer FAQ foundhere. We’ve been espousing its virtues ever since we’ve seen that this virus is no joke. There is a way of inocculating the area in which it operates, which requires some registry changes inside your workstation. The people at FOOLISHIT.COM (no joke either), have put together a little application to make this task a breeze.
What’s REALLY cool, is that some people have actually created DNS sinkholes out there, which are targetting the COMMAND and CONTROL servers that hand out the 2048bit keys. The sinkholes PRETEND to be the COMMAND and CONTROL domains, but don’t actually reply. If the virus can’t get the encryption key, it can’t encrypt your data and sits there in your system like a benign tumor. Yech.
Only problem? The DNS Sinkhole theory is not fast enough. Some of these viruses generate 50,000 new random domain names a day. Only a handful of them will actually have a real Virus server sitting at the far end. The people who create the sinkholes have to GUESS which ones are going to be used and then BUY the naming rights to that domain. That is a LOT of money thrown at this virus in hopes of stopping it. The next day? Same thing again. Yeesh.
One last bit of late breaking news, is that the “kidnappers” are now offering a late payment option of $2000 USD or 10 bitcoins to release the encryption key – in case you were late with the original payment. Ack!
Moral of the story? Don’t open attachments you weren’t expecting. Don’t go to random websites that may be infected. Get inocculated. Make sure your Windows 7 machine has its system protection turned on and there is at least 10GB dedicated to backups. Make a good backup of your machine and continue making them until you stop using that computer. Copy files that you create up to web services like Google Drive, Microsoft’s SkyDrive, Dropbox or get offsite backups created by our own GotData. Finally, if you can, get your IT provider to lock down your workstations, so that all users are restricted users (they can’t install or uninstall programs) and that programs are ONLY allowed to run from %programfiles%. That is the area that GOOD and PROPER programs run from. They CAN’T get in there, unless you explicitly allow them to do so.
So how has this changed the way we look at viruses for good? Easy. Up until this virus, most people and even service providers have seen viruses as annoyances. That at worst, they would be incapacitated for a day or two while their machine was fixed. A money maker, to be truthful. Both on the software side and the cleanup side. That backups were necessary, but frequent ones, not so much. This one virus changes all that. This one virus gets programmers rethinking that they had better start programming properly (into %ProgramFiles%) or their stuff just won’t be installed on user’s machines. This one virus has caused the lockdown of %APPDATA% and how Google Chrome gets installed – good luck with that one. This one virus has changed how we now look at the utility of ANTI-VIRUS programs which are in effect only BLACK LISTING bad programs they know about, vs WHITE LISTING good applications like Lumension has been doing for years.
Think About it. How many viruses do ANTI-VIRUS programs need to keep track of? Millions. How many applications do WHITE LISTING programs need to allow to run on your computer? A few hundred? Maybe a thousand or so? Which is easier to keep track of? A list that keeps on growing exponentially? Or one that you can actually read line by line in a single day?
Call your service provider to help you with this one. Or call Seerx. We’ve been battling viruses, restricting systems, working with backups, disaster recovery plans and getting computers and networks to work together for over 13 years. We’d love to help you stay up, all the time.